
Overview
Security Onion is a free and open platform built by defenders for defenders. It includes network visibility, host visibility, intrusion detection honeypots, log management, and case management.
For network visibility, we offer signature based detection via Suricata, rich protocol metadata and file extraction using your choice of either Zeek or Suricata, full packet capture via Stenographer, and file analysis via Strelka. For host visibility, we offer the Elastic Agent which provides data collection, live queries via osquery, and centralized management using Elastic Fleet. Intrusion detection honeypots based on OpenCanary can be added to your deployment for even more enterprise visibility. All of these logs flow into the Elastic stack and we've built our own user interfaces for alerting, hunting, dashboards, case management, and grid management.
Security Onion has been downloaded over 2 million times and is being used by security teams around the world to monitor and defend their enterprises. Our easy-to-use Setup wizard allows you to build a distributed grid for your enterprise in minutes!
Highly Scalable
From a single network appliance, to a grid of a thousand nodes, Security Onion scales to fit your specific needs.
Open Community
Security Onion and the tools we integrate are all open to the public, written by members of the cyber security community. Source code is available in GitHub for review by those interested in understanding how the system works, behind the scenes.
Collect network events from Zeek, Suricata, and other tools for complete coverage of your network. Cast a wide net to catch the bad guys quickly and easily.
Security Onion supports Elastic Agent for event collection on your organization's endpoints. Simply install the agent package available in the SOC Downloads page!
Use Security Onion to import full packet capture files and Windows Event log files for quick static analysis and case studies. Spin up a virtual machine quickly and get started in just a few minutes!
A Linux desktop install option is also available for SOC analysts to use local Linux tools to perform analysis of network and host events. No need to install extra tools; we bundle all the apps you might need.
Included Features
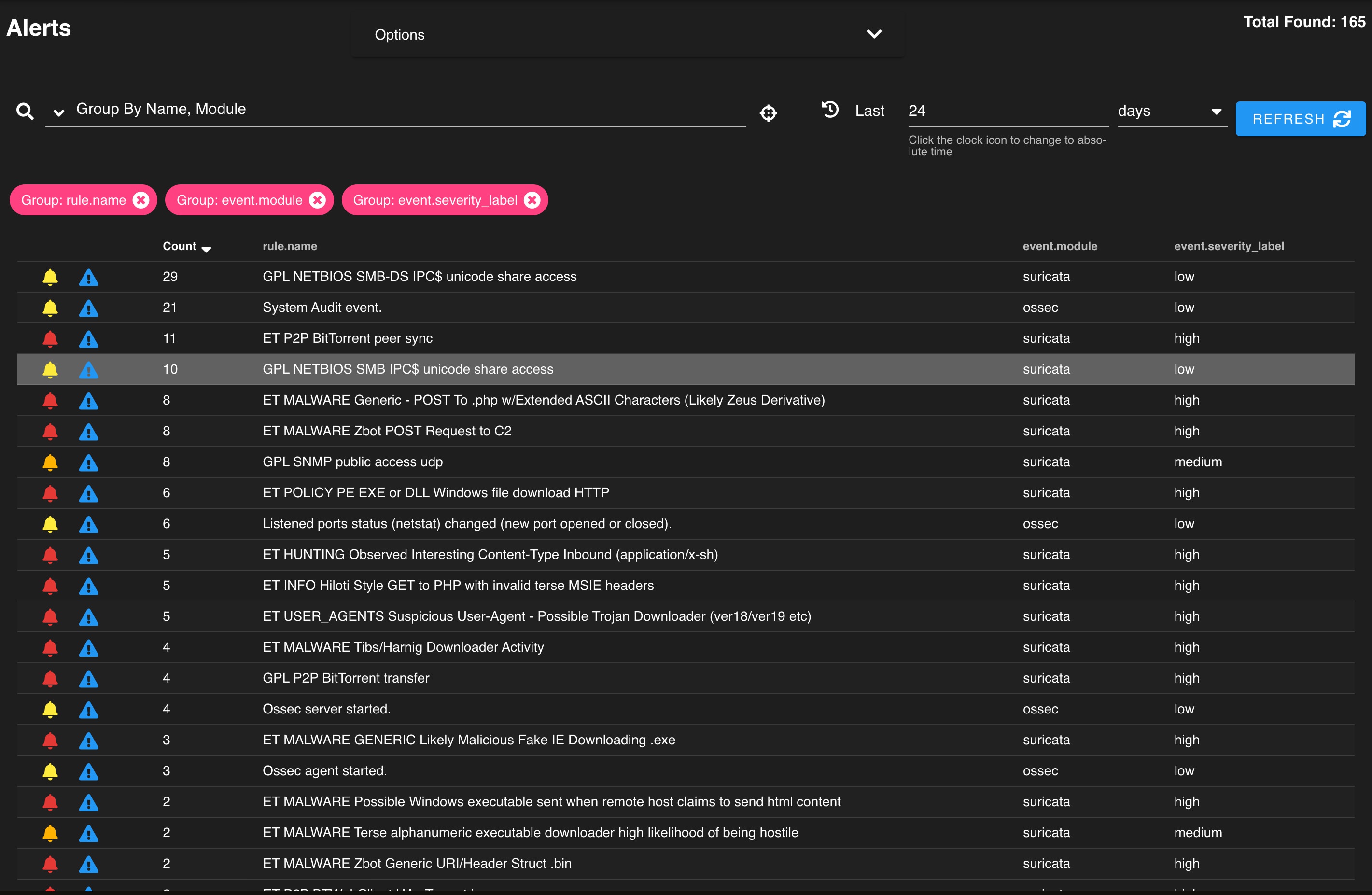
Use our Alerts interface to review and manage alerts generated by Security Onion.
Data Types
Agent
Information gathered from agent software
Elastic Agent
Alert
Judgment made by a product about an event
Suricata
Asset
Metadata about hosts on the network
Zeek
Extracted Content
Rebuilt elements of a session and extracted metadata
Zeek
Full Content
All packets on the network
Stenographer
Session
Detail about conversations between hosts
Zeek, Suricata
Transaction
Generated logs based on network traffic protocols
Zeek, Suricata
Let Security Onion Solutions take care of the hardware and setup, so you can focus on threat hunting.